Soham Parekh is a developer that managed to hold down multiple remote jobs at a number of VC-backed startups all at the same time. That is, until yesterday when one founder posted this:
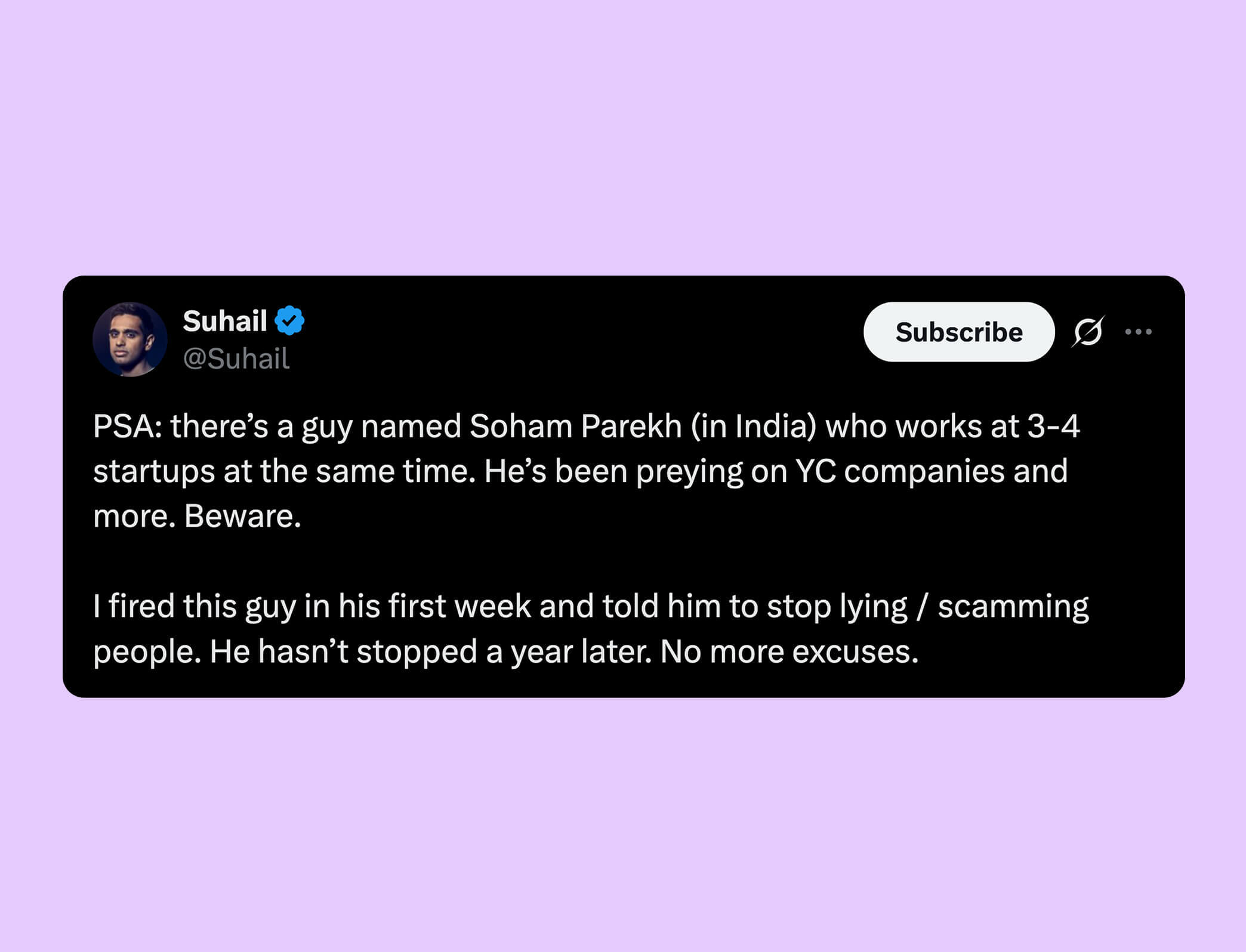
For the rest of the day, Soham was the talk of Twitter (or X, whatever). Some people were impressed that Soham could pull it off. Others labelled him a scam artist and said he should be ashamed. There was even a group that thought Soham did nothing wrong, given that the startups that hired him seemed to not notice.
To be blunt, there is nothing interesting about Soham himself. You mean to tell me that some people commit fraud? Scams are real? Not everyone tells the truth? Wow. Shocking. However, what is interesting is the number of startups that fell for Soham's scam. If you read the discussion online, you might be led to believe this could happen to anyone. He interviewed well! He had good references! How could anyone have known?
This is nonsense. If your company hired Soham, then your cybersecurity posture is extraordinarily weak, and your customers and investors should be very concerned. That is the topic of this blog post.
How Is This a Cybersecurity Issue?
Hacking is hard. You have to find some technical vulnerability, exploit it, and then go undetected while you engage in some malicious activity. It’s way easier to socially engineer your way into a company. Usually that involves tricking an employee to hand over their credentials, but it could also look like what Soham did: Convince a company to hire you and give you the access you need.
There’s no evidence to suggest that Soham did anything malicious like stealing company data, but that is really just a matter of luck. The person who first exposed Soham admits that Soham lied about his location (claiming to be in the US when he is in India), and that they even shipped a laptop to a US address.
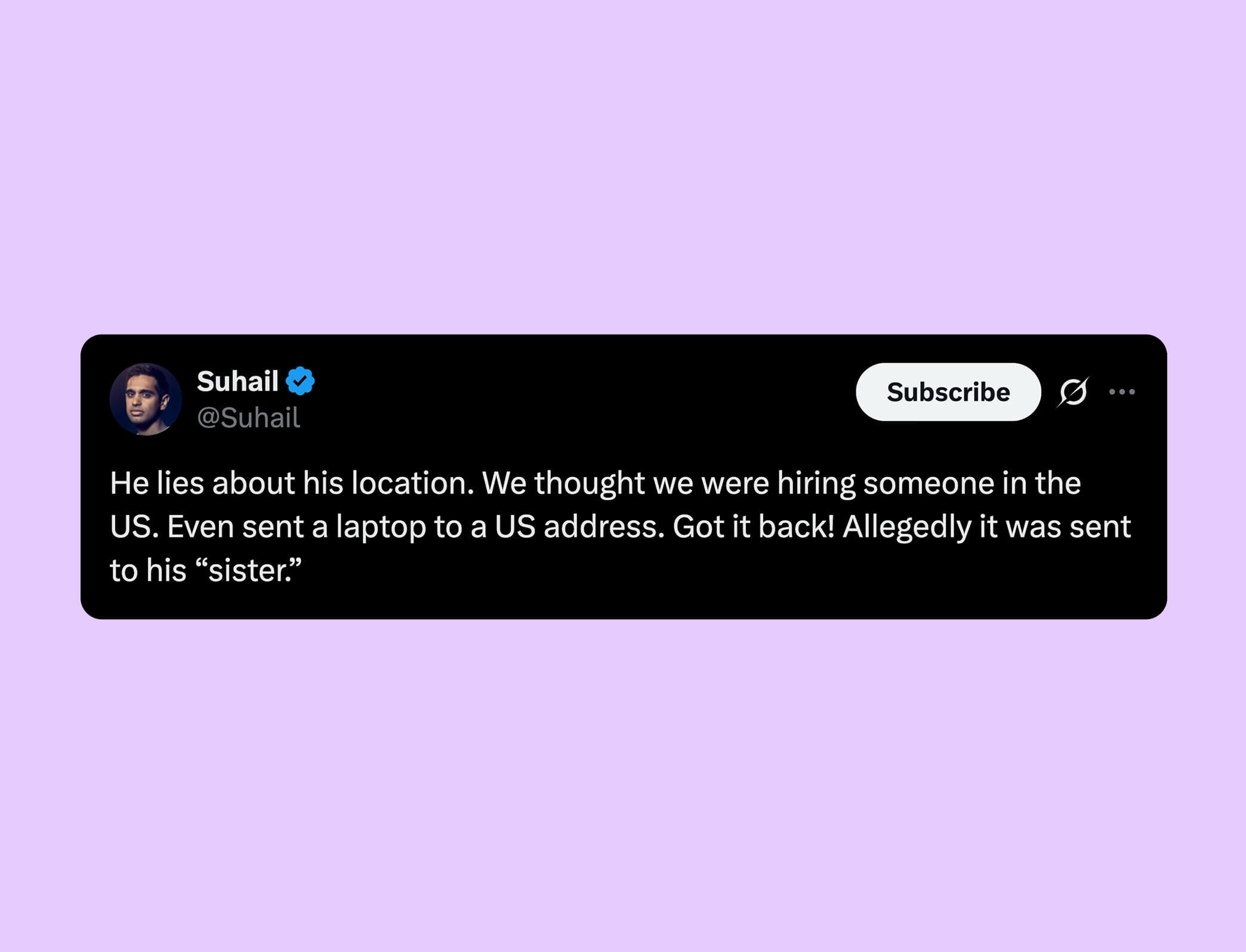
This is basically identical to what happened with KnowBe4, a security awareness company that hired a North Korean threat actor. They also shipped a laptop to a US address before discovering the fraud. And it turns out this is more common than you might think.
If you are hiring people that you don’t know and can’t verify the identity of and shipping laptops to unknown addresses, it doesn’t matter how good your cybersecurity is otherwise. Every one of your employees is a potential cybercriminal, and you are paying them for the privilege of hacking you.
Avoiding Fraudulent Employees
If you read the comments online, you might believe that this is a hard case to detect. How were these startups ever meant to catch this? As it turns out, it’s extremely easy.
First, if you want to make it really easy, just don't hire fully remote employees. Done. At Pistachio, every person we hire on the tech team goes through an in-person interview and also is required to be at the office at least two days per week. Am I missing out on the best talent available in the global workforce? Maybe, but I am not the one who hired Soham either, so let’s not pretend that these startups are somehow elite talent scouts.
Second, a copy of the (likely fake) CV that Soham used is available online, as it was shared by a startup that hired him. It is full of red flags.

According to his CV, he started a job as a senior software engineer at Synthesia, a fast-growing scale-up that is now a unicorn, while still doing his master’s degree. That already looks very odd. Then he chose to leave that rocket ship for some reason to go to a relatively unknown union.ai for the same position. Very odd. He also job hops every year on the dot, and lists so many different technologies that it is extremely unclear what he really knows.
There is no way I would invite this person to an interview. But just to make sure, I also asked our VP of Engineering to take a look, as he hasn’t heard of Soham.[1] He immediately flagged that the guy is a job-hopper, fully remote, and has such a huge spread in his technology stack that it looks fake.
So without running background checks, without calling references, without digging into his backstory in an interview, and without sleuthing through his social media presence, we can easily see that we shouldn’t hire this person.
Accountability
I’m not going to reveal the name of every startup that came forward to say that they worked with Soham, but the founders and senior managers of those companies should take some time to reflect internally. There will always be people who try to scam you; it is your job to defend against that.
If you are a customer that is sharing data with one of these startups, you should probably stop.[2] This is a canary in the coal mine. They’re telling you that they don’t have basic operational safeguards in place, and that needs to change.


