What are you
interested in?
Category
All
Tags

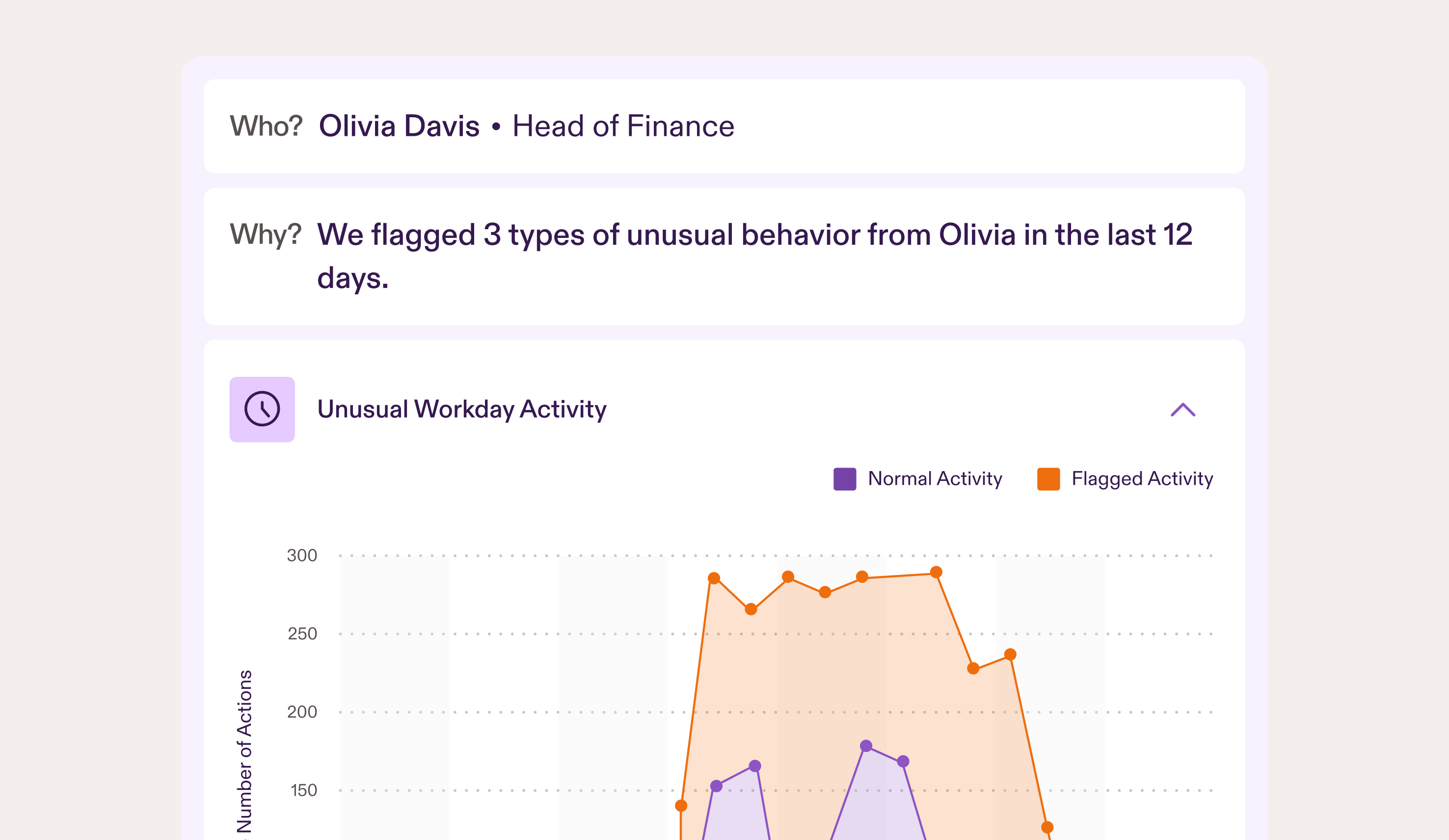
Protecting IP During High-Growth: Why Scaling SaaS Companies Can't Ignore Insider Risk
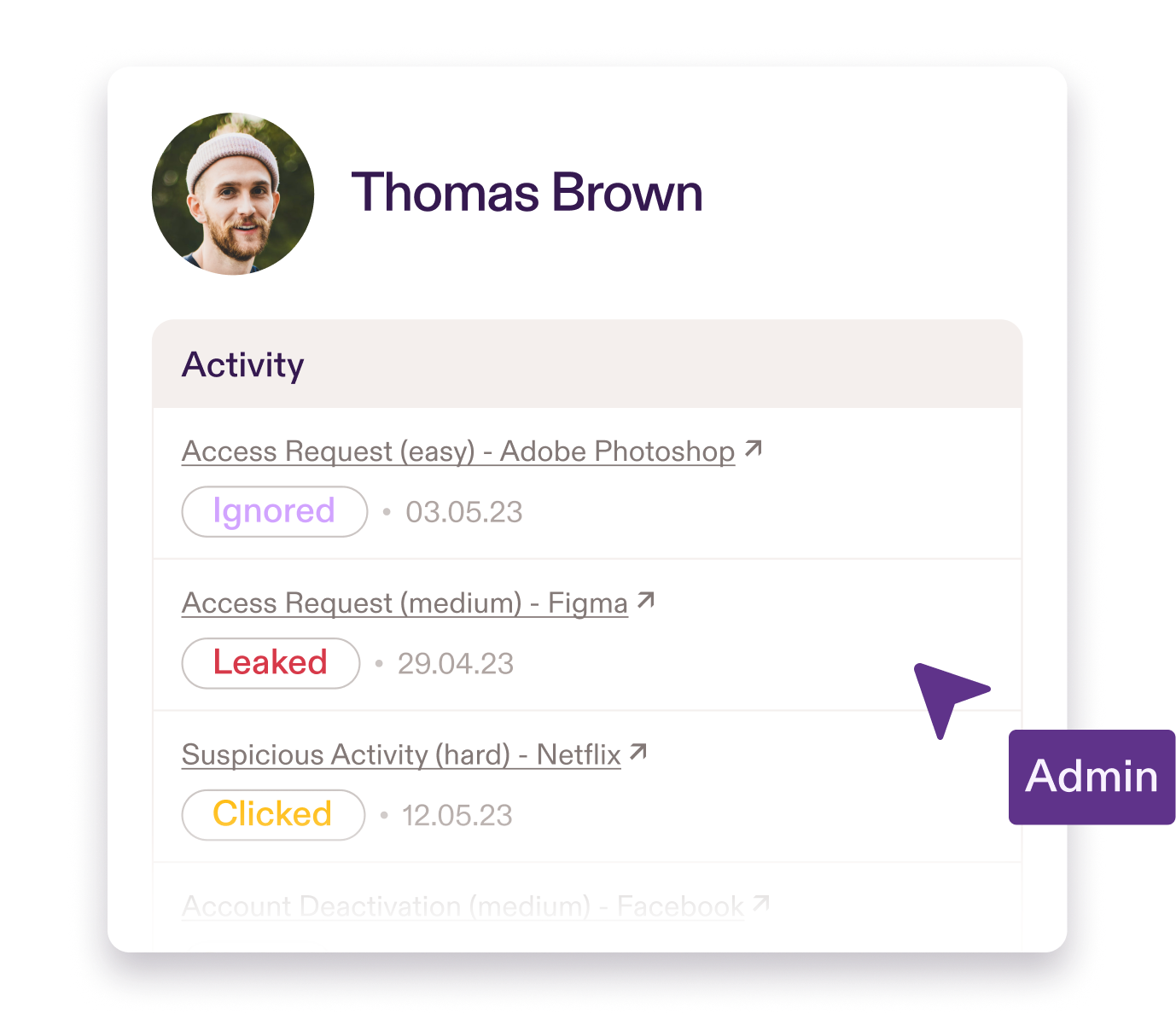
Insider Threat Scenarios You Can't Afford to Ignore
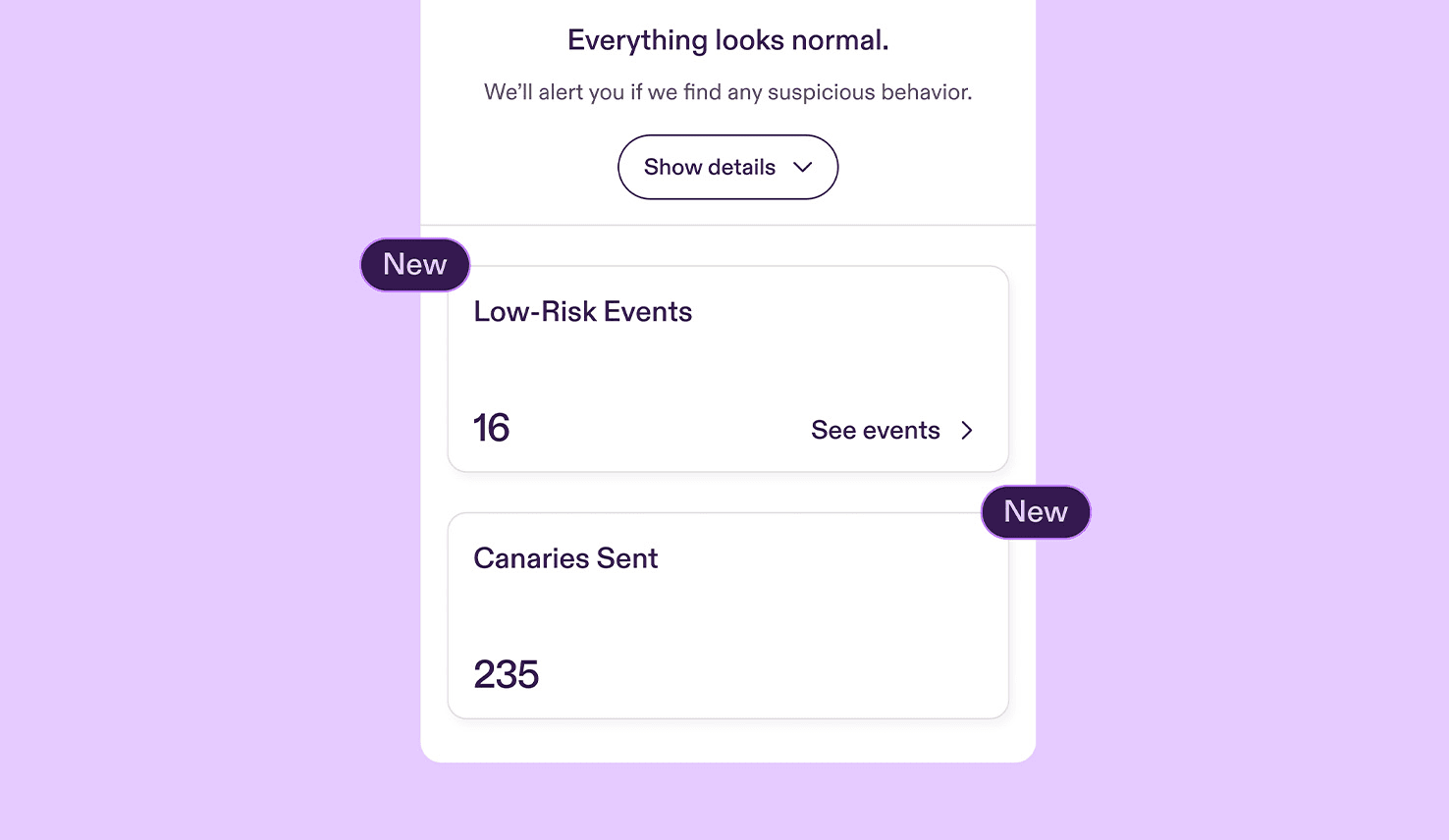
New Features: Canaries and Low-Risk Events
You, Me, and Data Denormalization
Written by Kasper Rynning-Tønnesen
Pistachio Presence: The New Era of Insider Threat Detection

Meet Michael: A people person who unwinds by diving into new worlds

Copilot Broke Your Audit Log, but Microsoft Won’t Tell You
Written by Zack Korman

The Case of Soham: The Cybersecurity Risk of Bad Hiring Practices
Written by Zack Korman

Meet Oleksandr: A creative mind cooking up great design and delicious meals
Cybersecurity training integrated with your team’s go-to apps

Try-catch; The GOTO that Needs to GOAWAY
Written by Kasper Rynning-Tønnesen
Pistachio Loop: Your regular check-in with cybersecurity
We believe in a learn-by-doing approach over snooze-worthy videos.
Instead, Pistachio tailors real-world scenarios so your team can build their cyber skills in a safe environment.